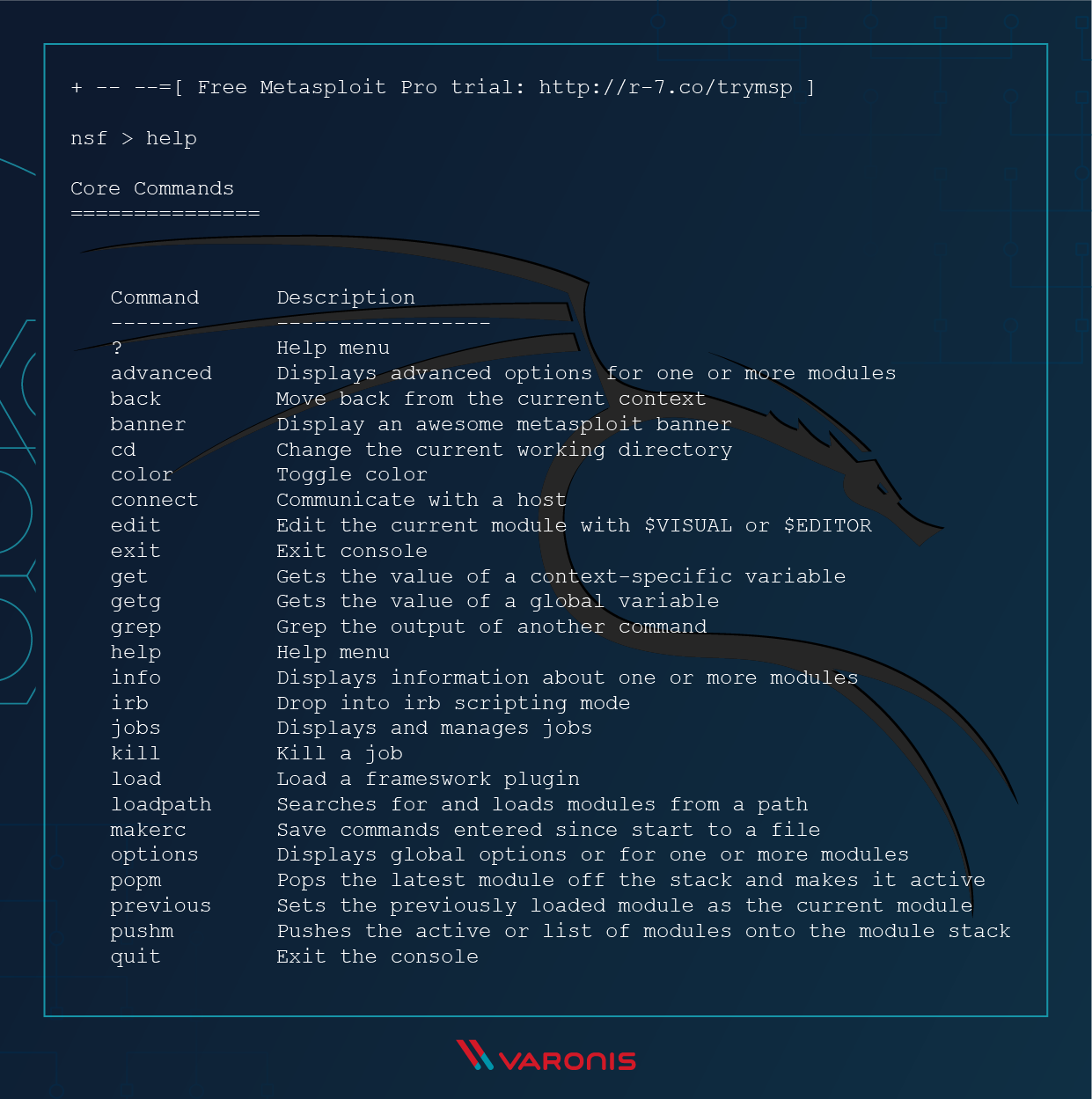
Kali Linux: Zaawansowane testy penetracyjne za pomocą narzędzi Nmap, Metasploit, Aircrack-ng i Empire : Singh, Glen D.: Amazon.es: Libros

Stephen Fewer on X: "and now we've added an RCE exploit module for this too... https://t.co/qfqxMyiB5Q" / X


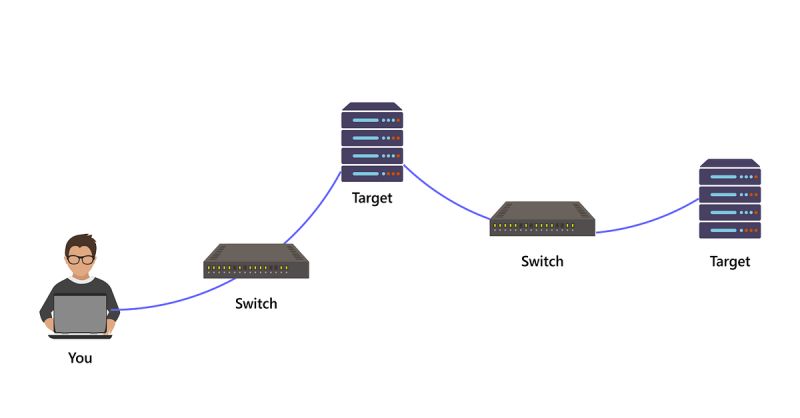



_mobile.jpg)


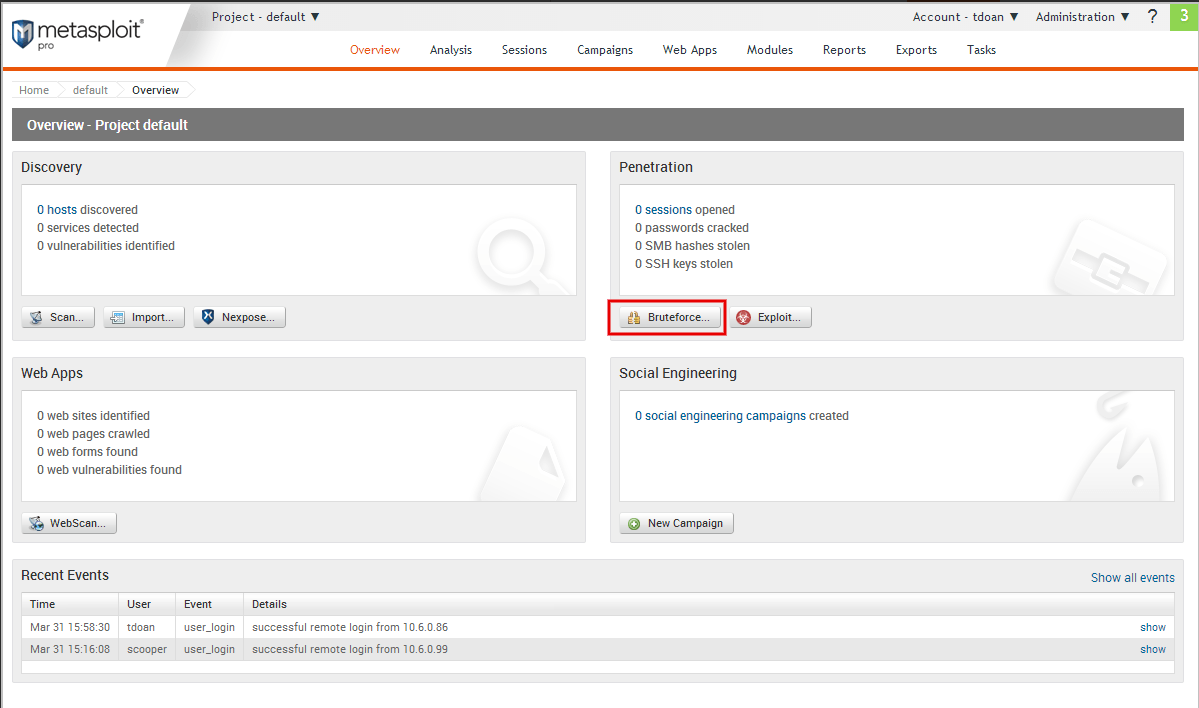
![How to do it... - Metasploit Penetration Testing Cookbook - Third Edition [Book] How to do it... - Metasploit Penetration Testing Cookbook - Third Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781788623179/files/assets/bcb894af-94cf-486d-ab64-6b09d0d7bc98.png)