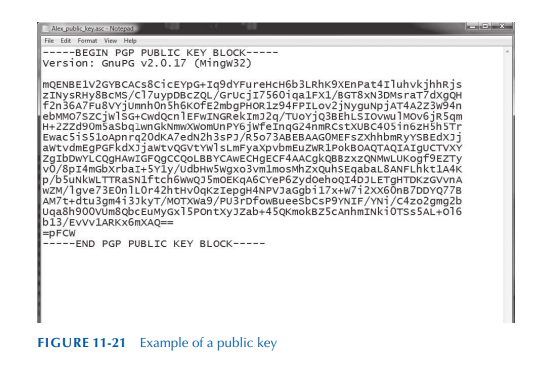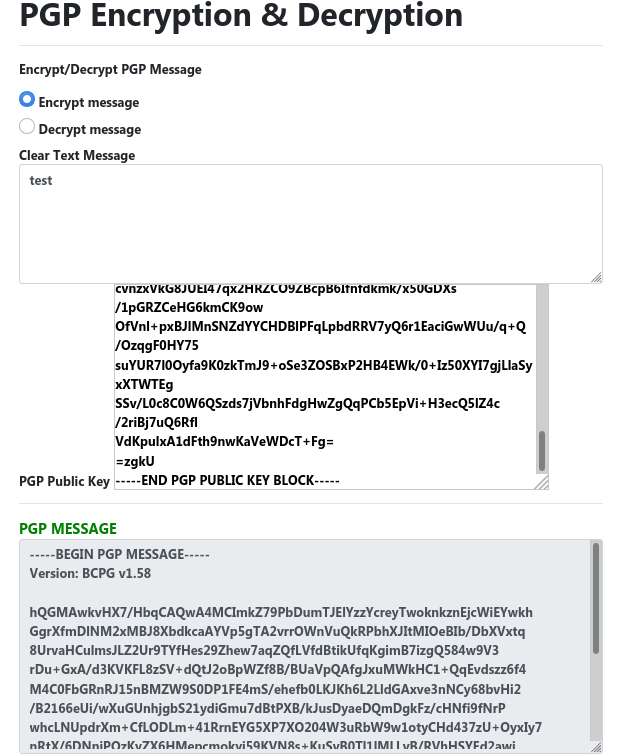
How To Make a PGP Keypair using GPG and Communicate In Absolute Privacy (Linux/Mac) Public & Private Keys + Encrypt & Decrypt Messages - Sick Codes - Security Research, Hardware & Software
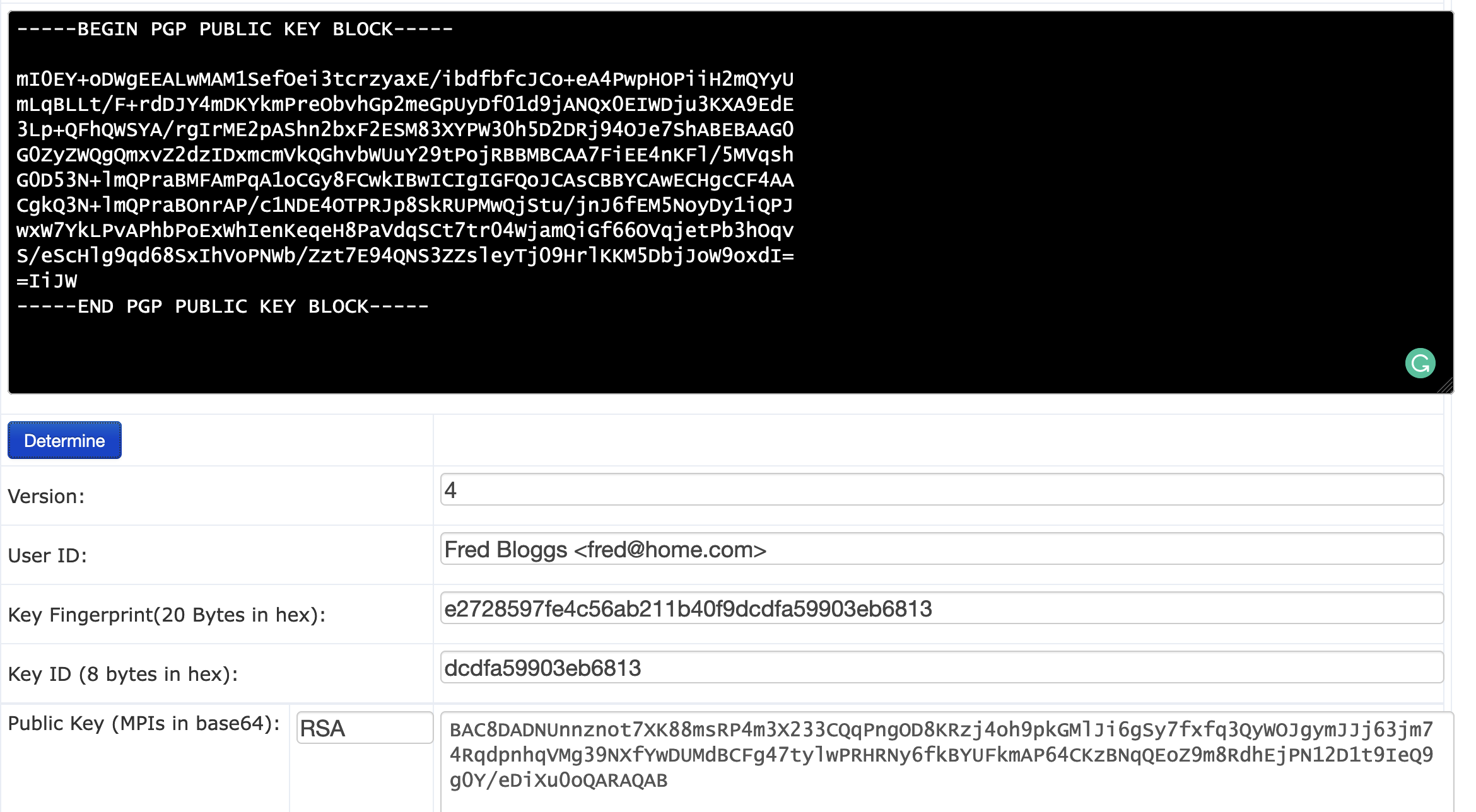
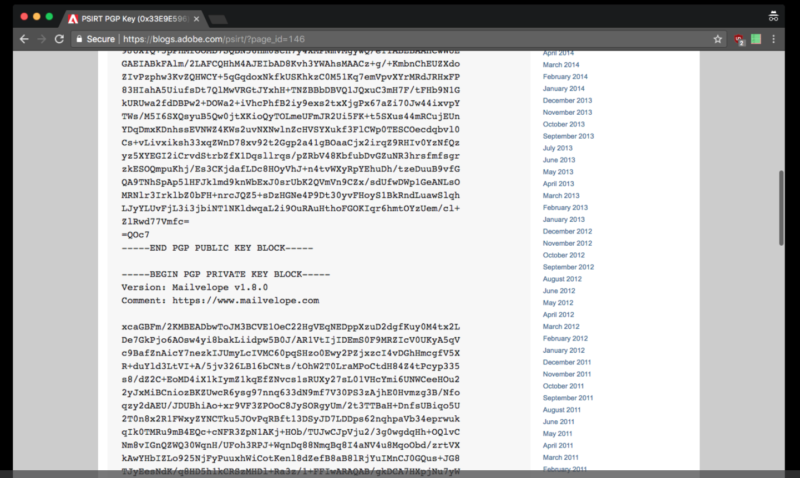
![cryptography - How to get v12.0 to print PGP public key and secret key BLOCKS after generating a key pair using GenerateAsymmetricKeyPair[]? - Mathematica Stack Exchange cryptography - How to get v12.0 to print PGP public key and secret key BLOCKS after generating a key pair using GenerateAsymmetricKeyPair[]? - Mathematica Stack Exchange](https://i.stack.imgur.com/AZsn3.png)
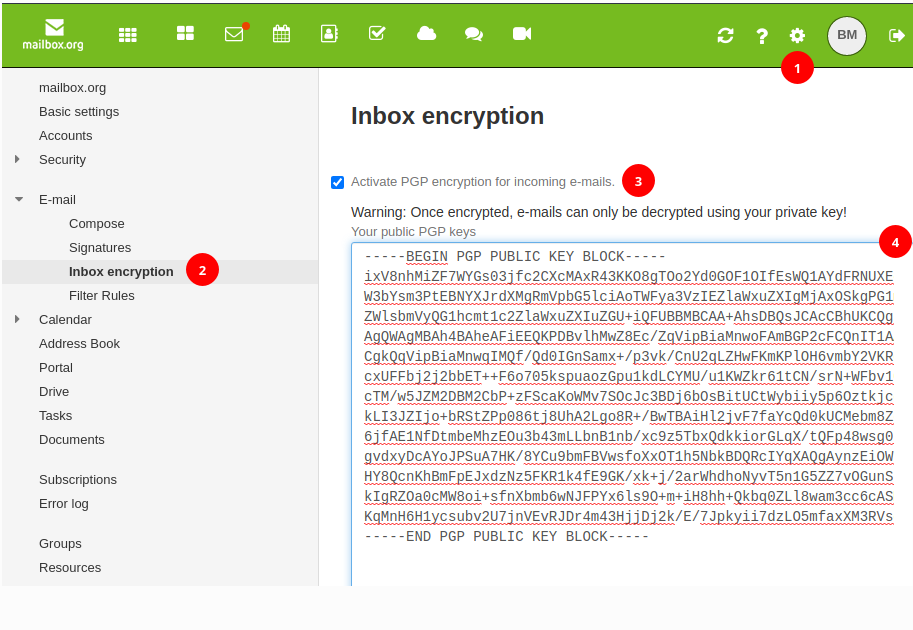
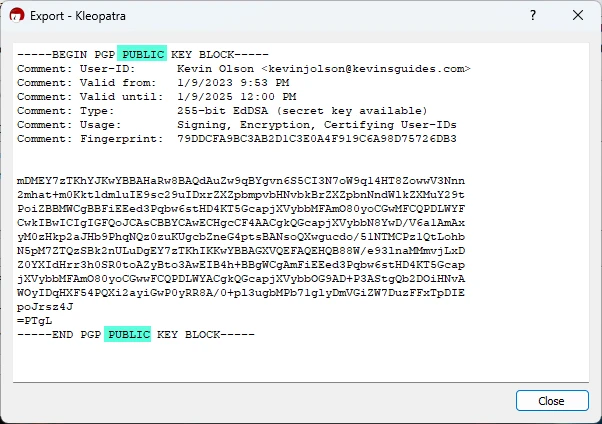
cryptography - How to get v12.0 to print PGP public key and secret key BLOCKS after generating a key pair using GenerateAsymmetricKeyPair[]? - Mathematica Stack Exchange
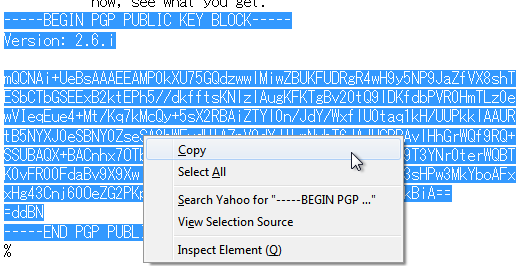

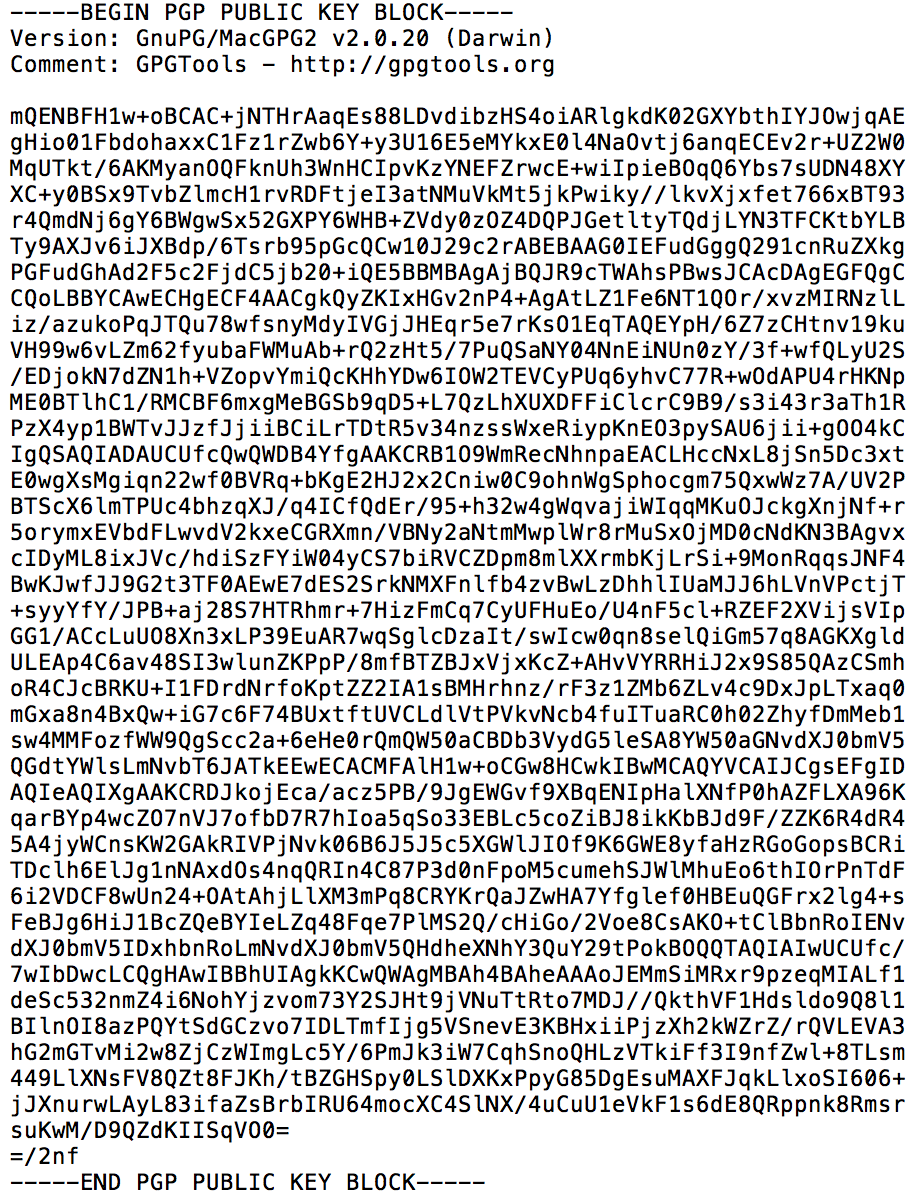
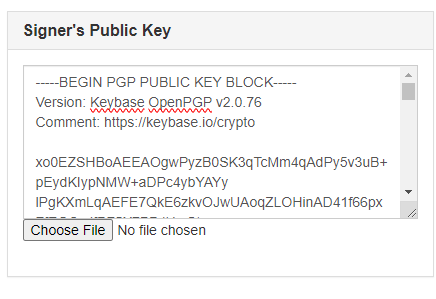
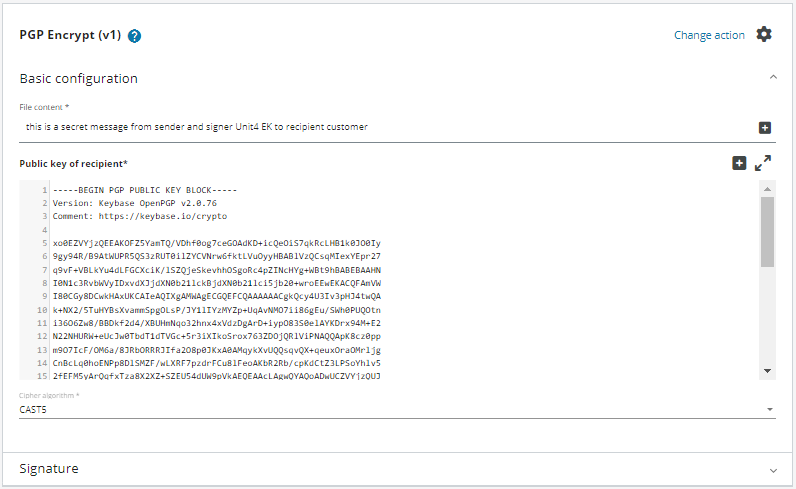

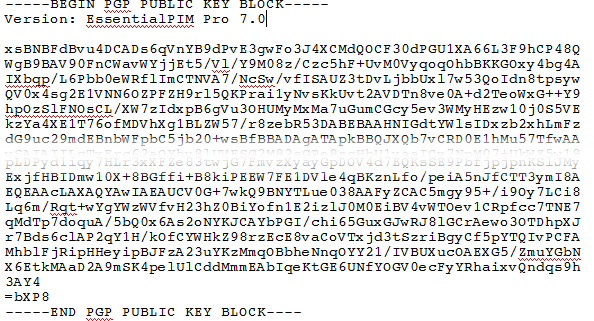
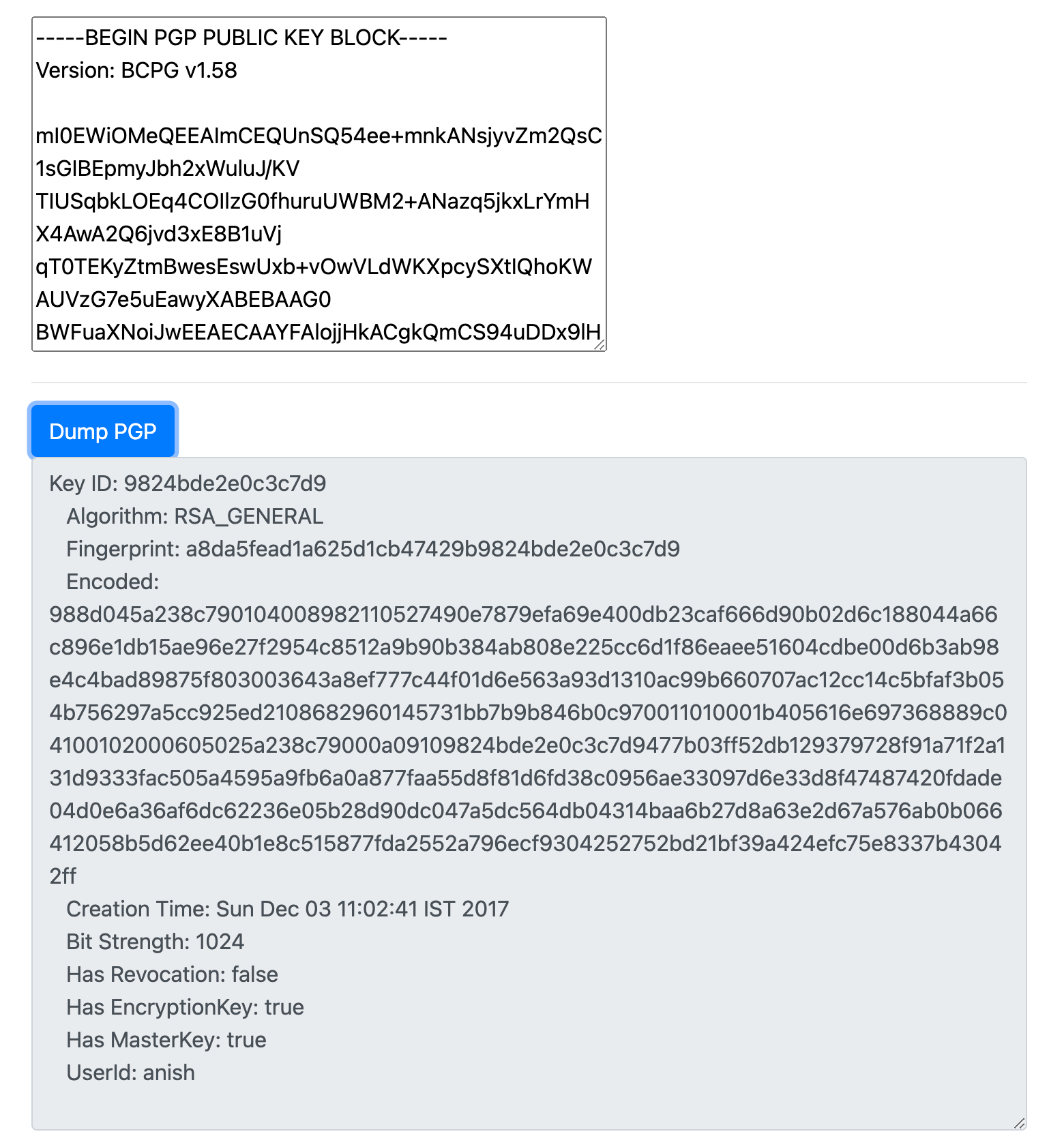

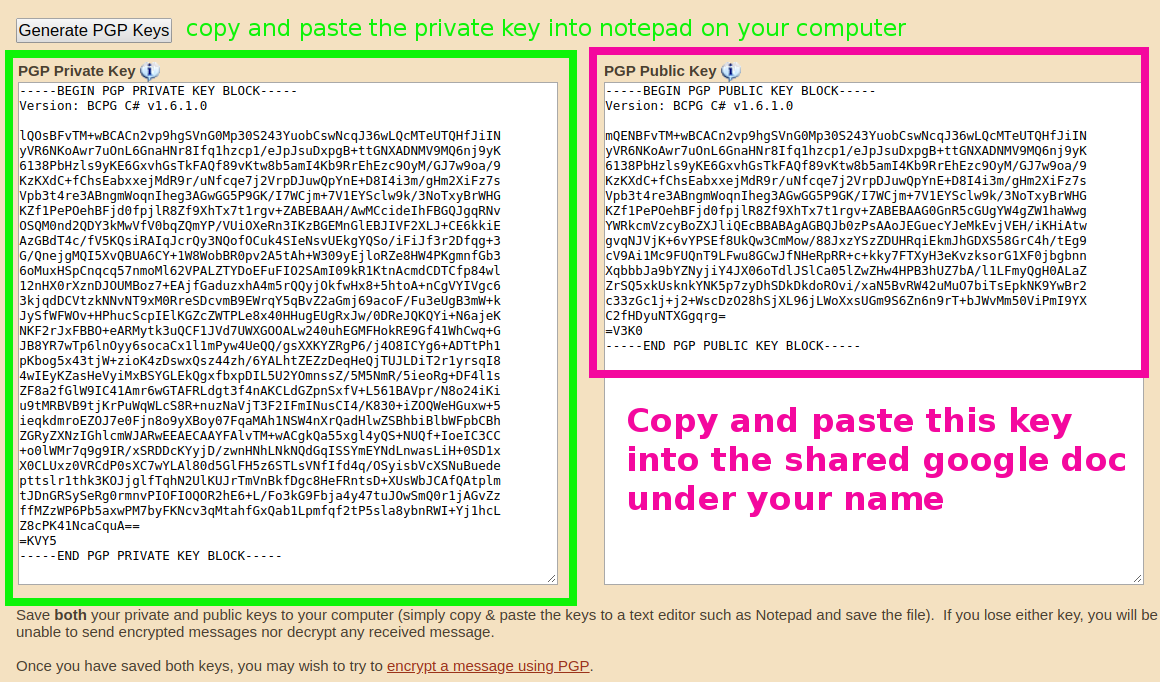
![Tutorial] How do PGP keys work - Jacob Riggs | Blog Tutorial] How do PGP keys work - Jacob Riggs | Blog](https://jacobriggs.io/blog/app/web/upload/misc/pgp-encryption-diagram.png)
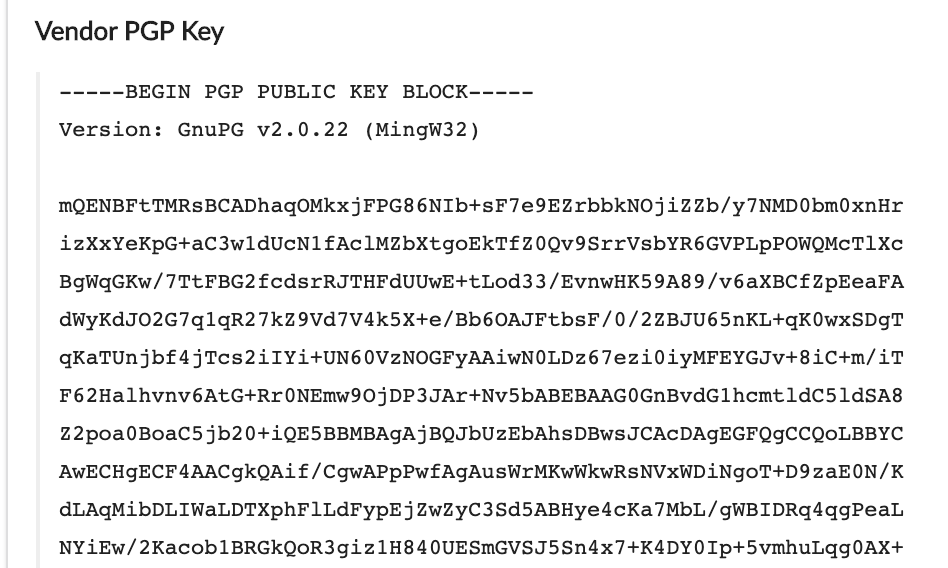
![What's the matter with PGP? ― Some Comments [The Call of the Open Sidewalk] What's the matter with PGP? ― Some Comments [The Call of the Open Sidewalk]](https://articles.59.ca/lib/exe/fetch.php?tok=bf1cfe&media=https%3A%2F%2Fmatthewdgreen.files.wordpress.com%2F2014%2F08%2Fba0d3-keys.png)