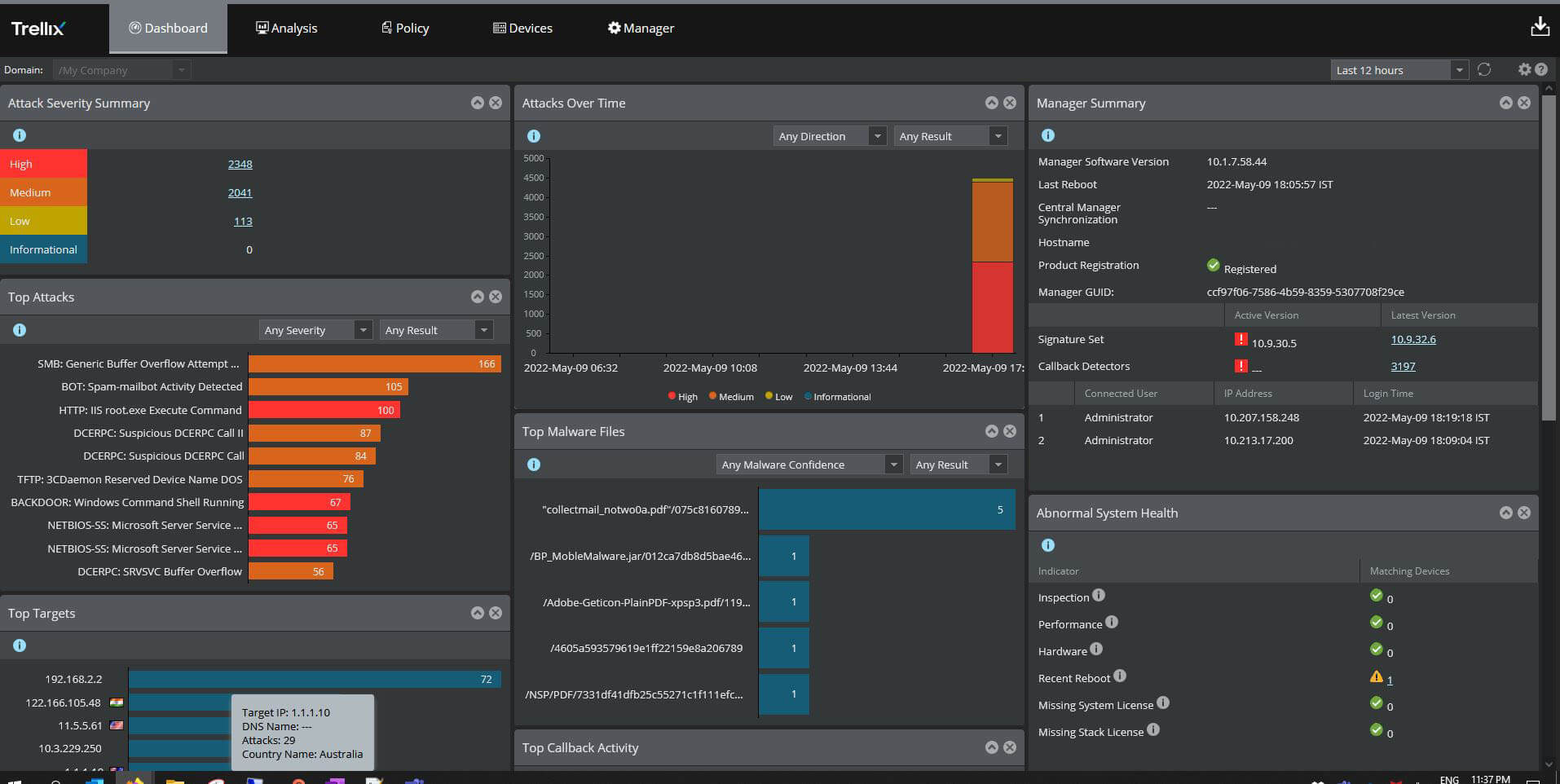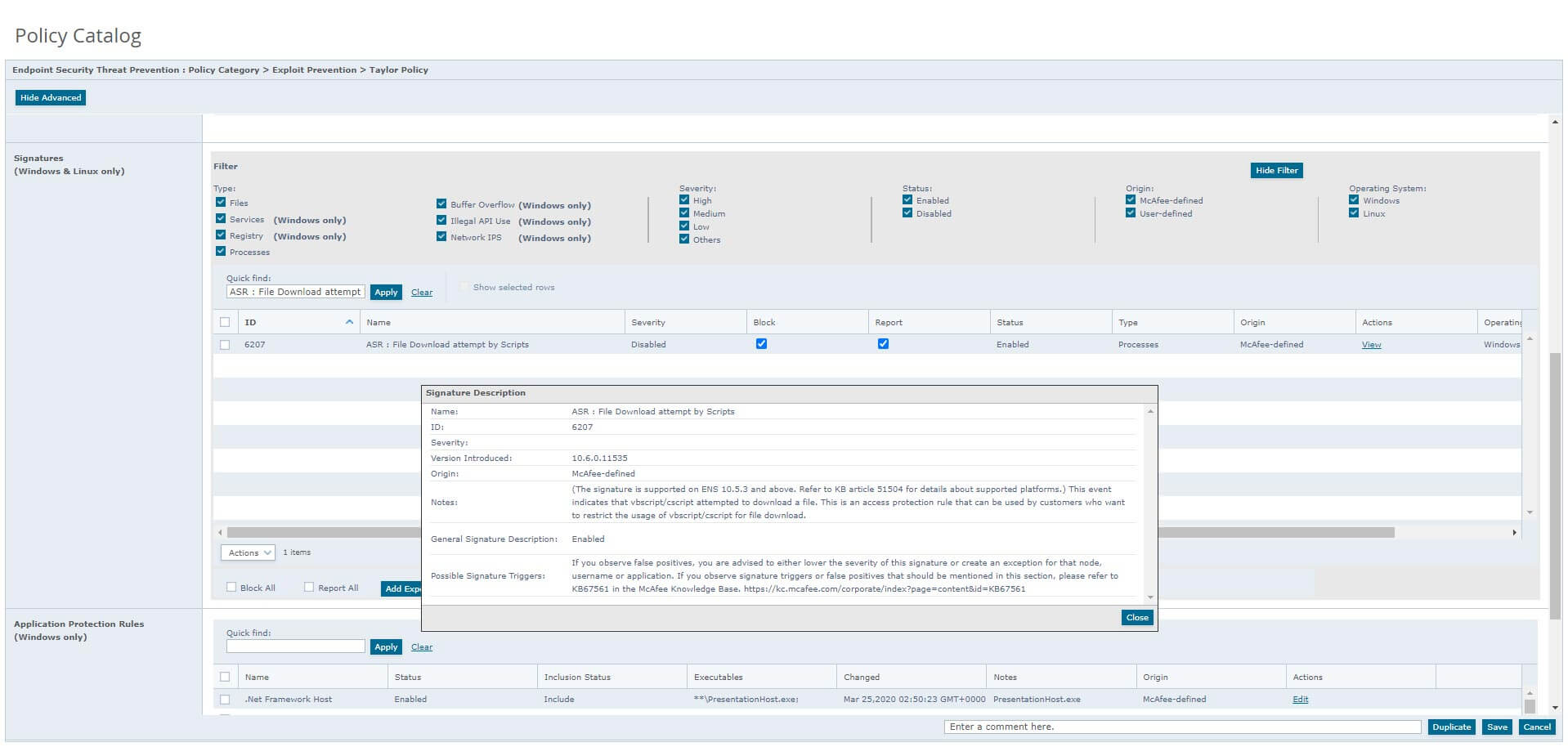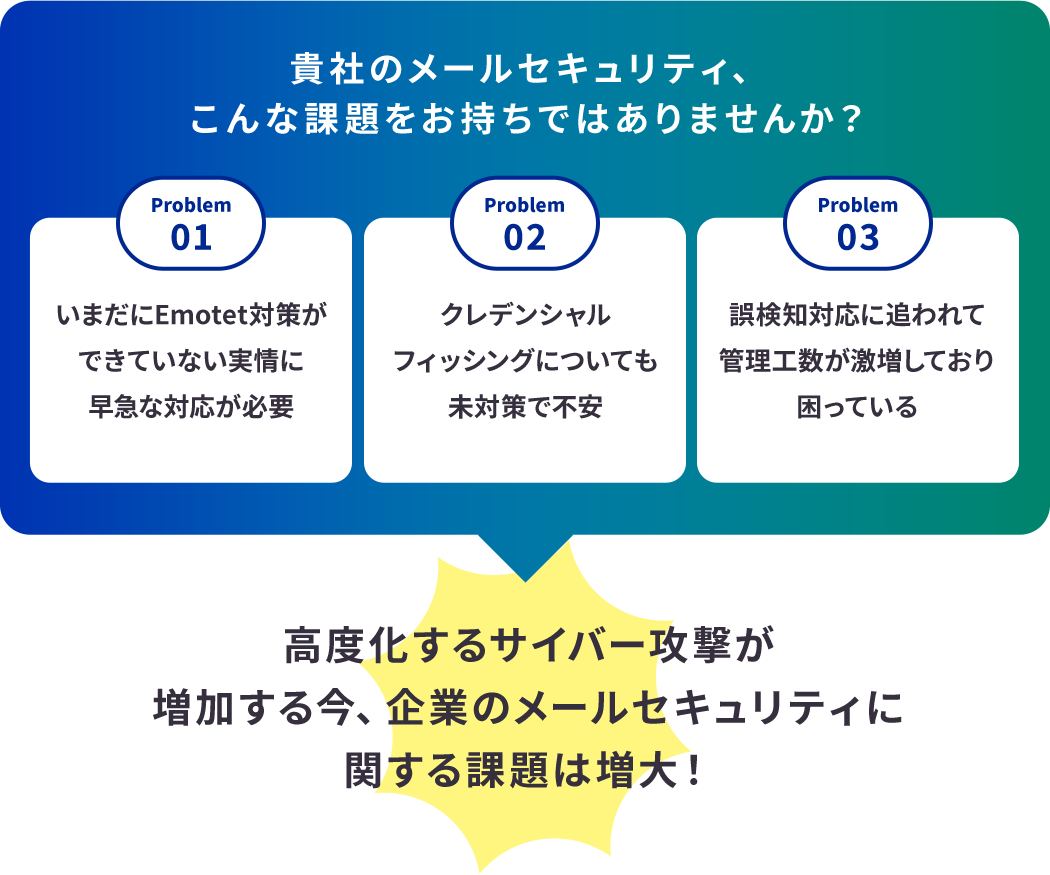
For targeted email attack countermeasures, use "Trellix (formerly FireEye) Email Security" -Macnica, Inc.

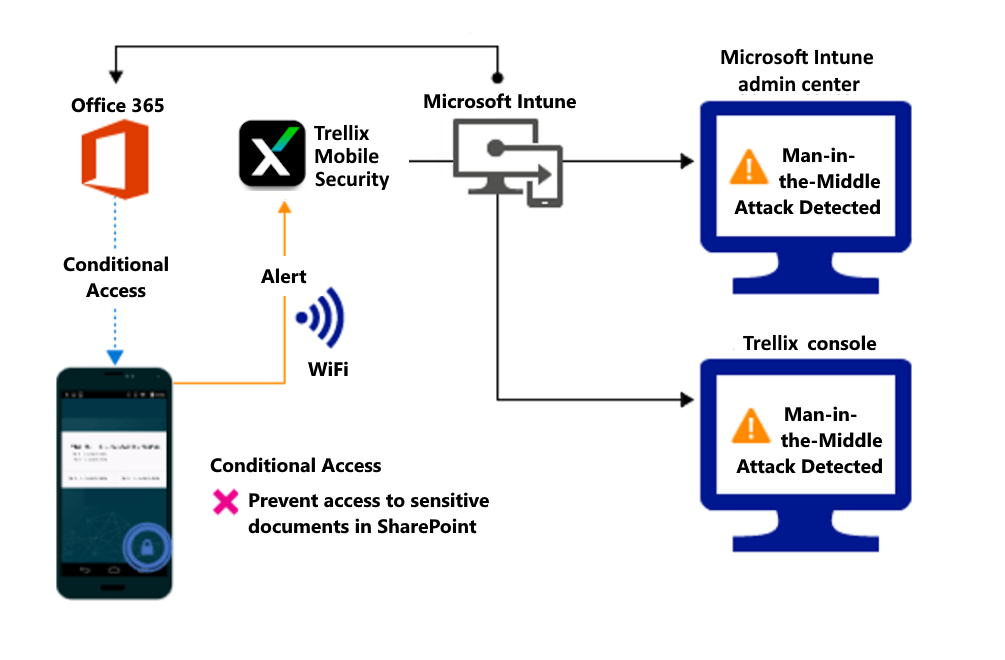
Trellix Email Security – Cloud: Adaptive protection that identifies, analyzes, and blocks email attacks - AlJammaz Technologies
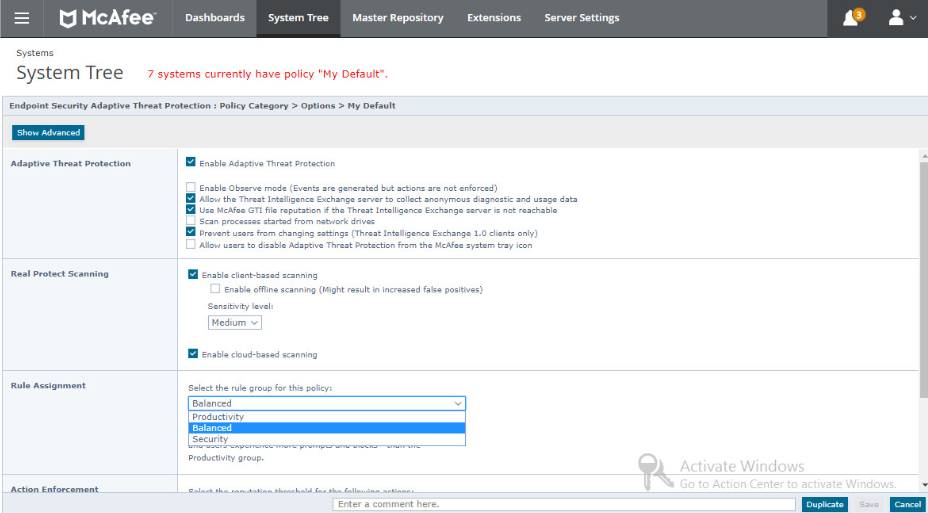
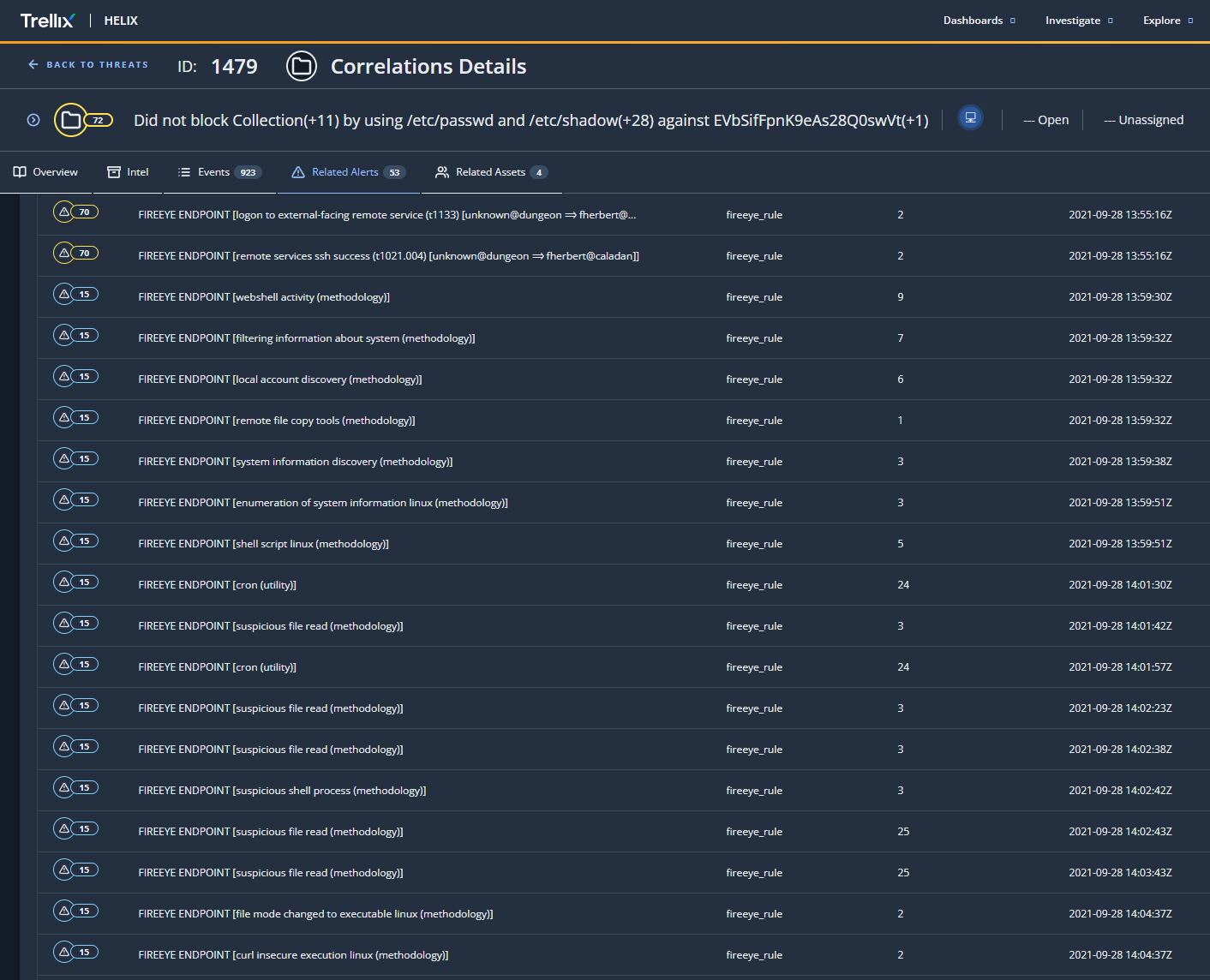
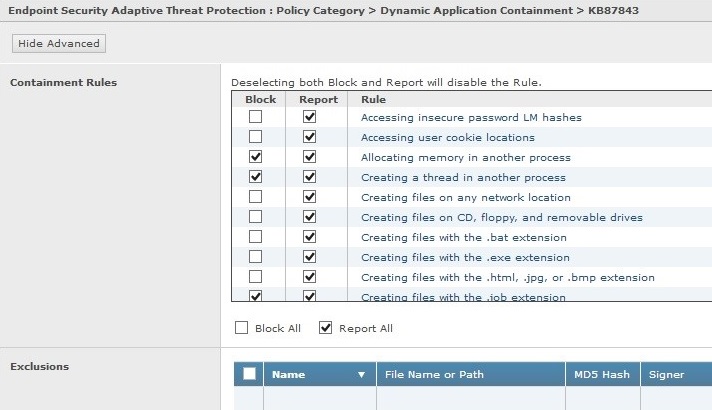
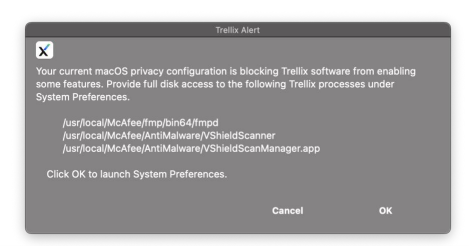
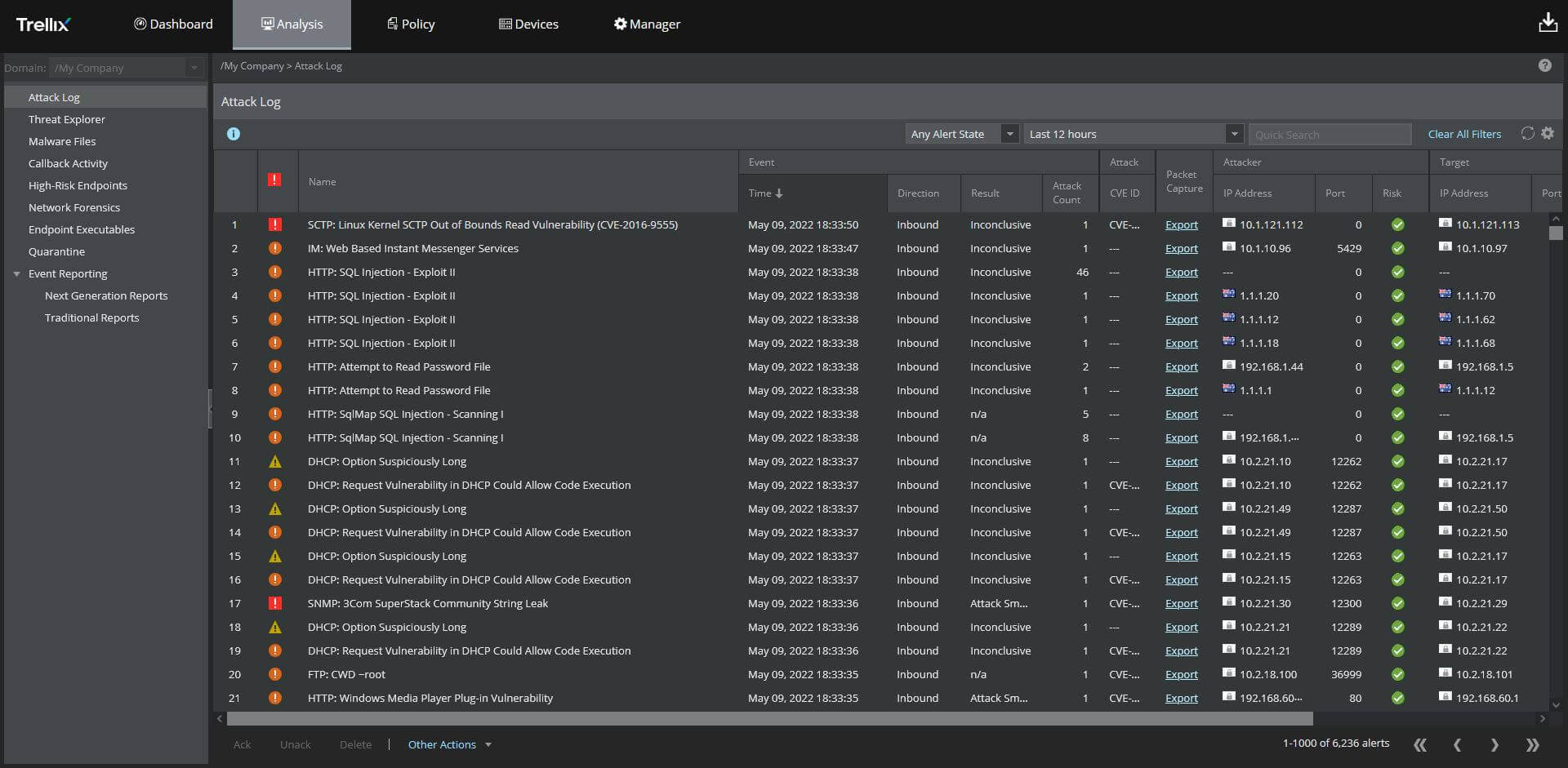
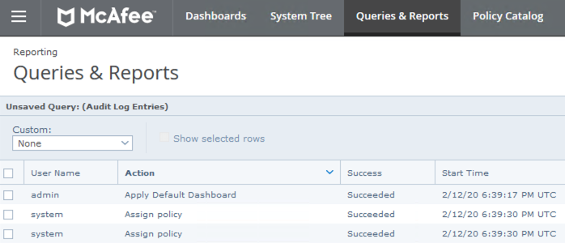
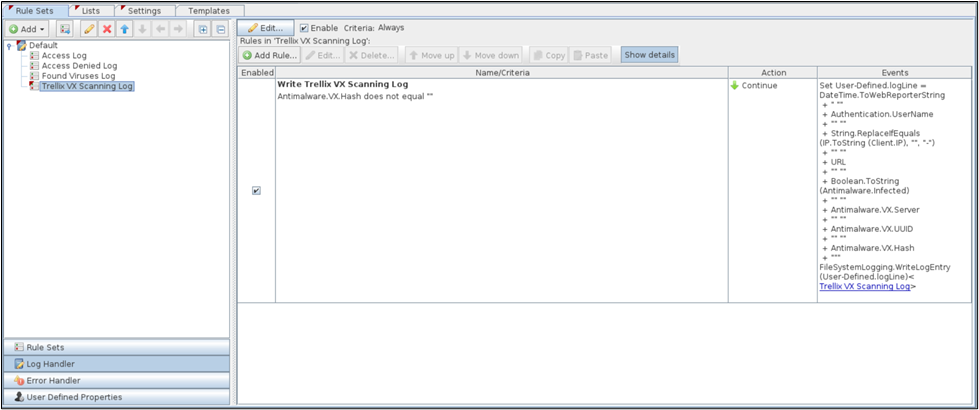
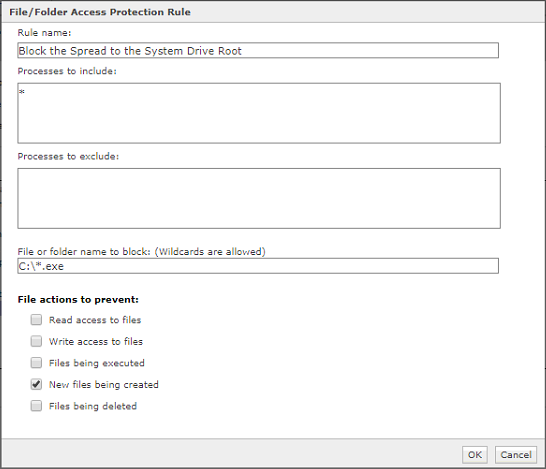
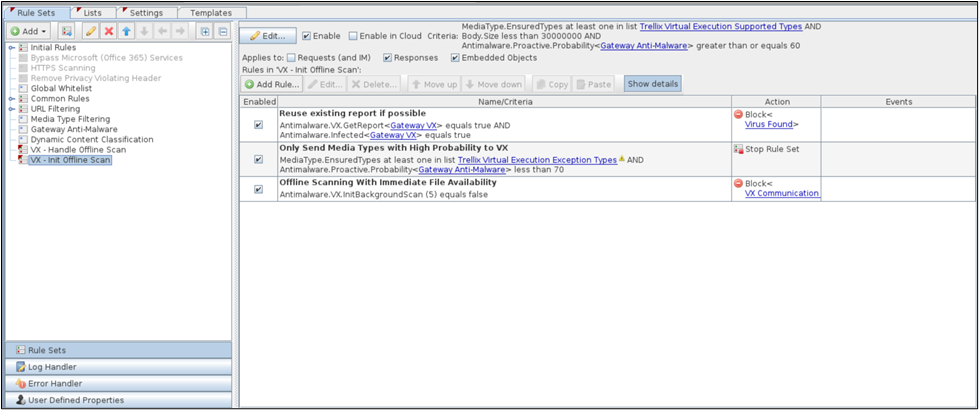
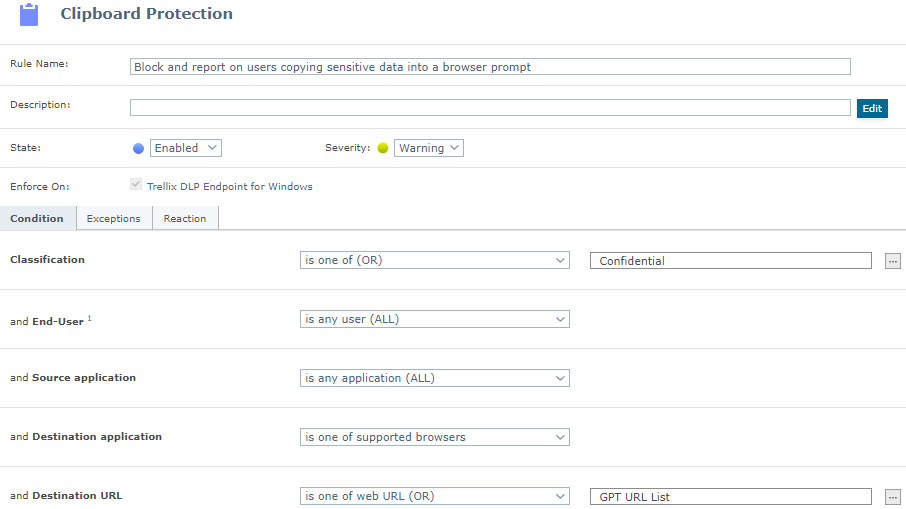
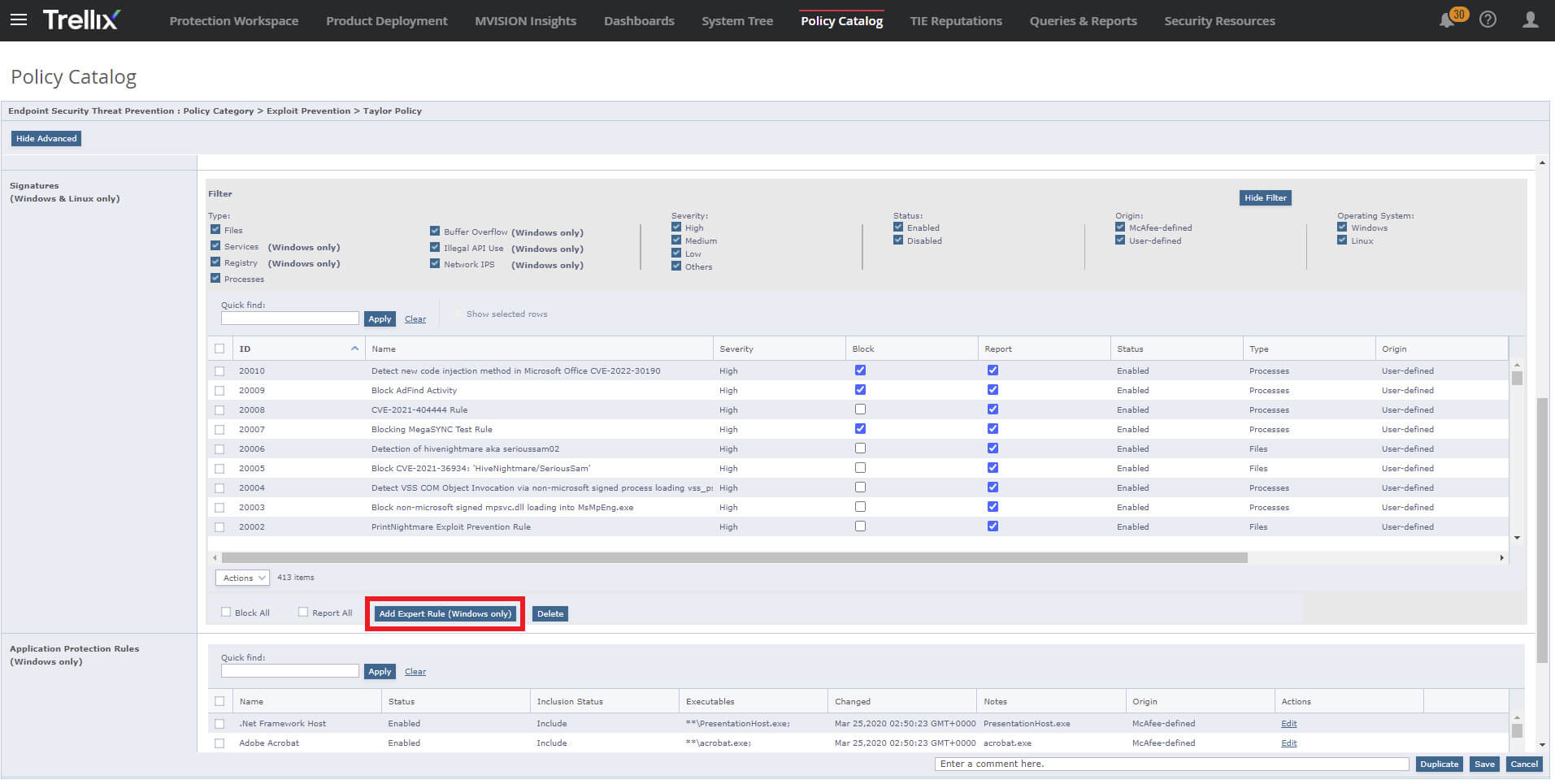
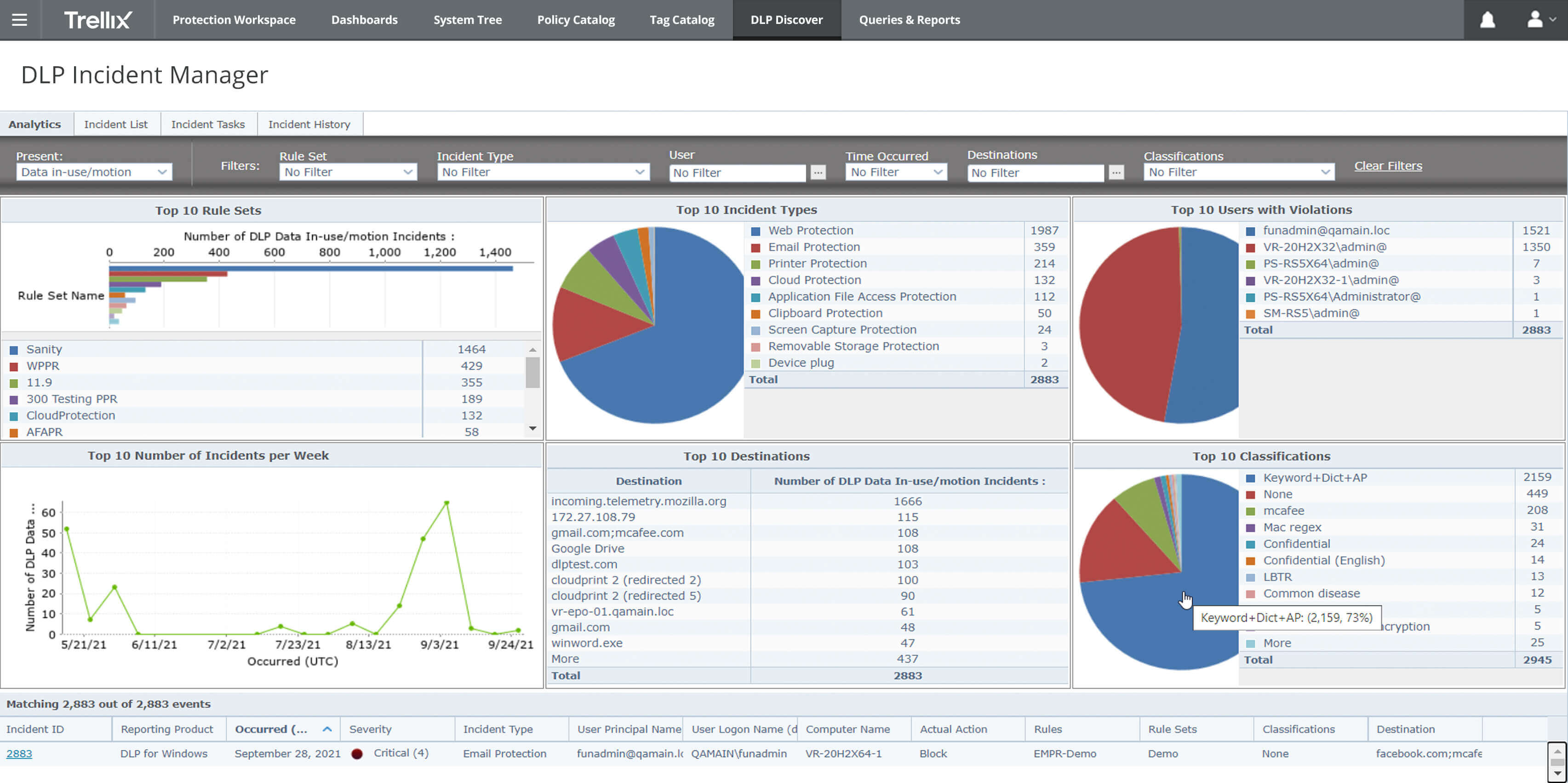
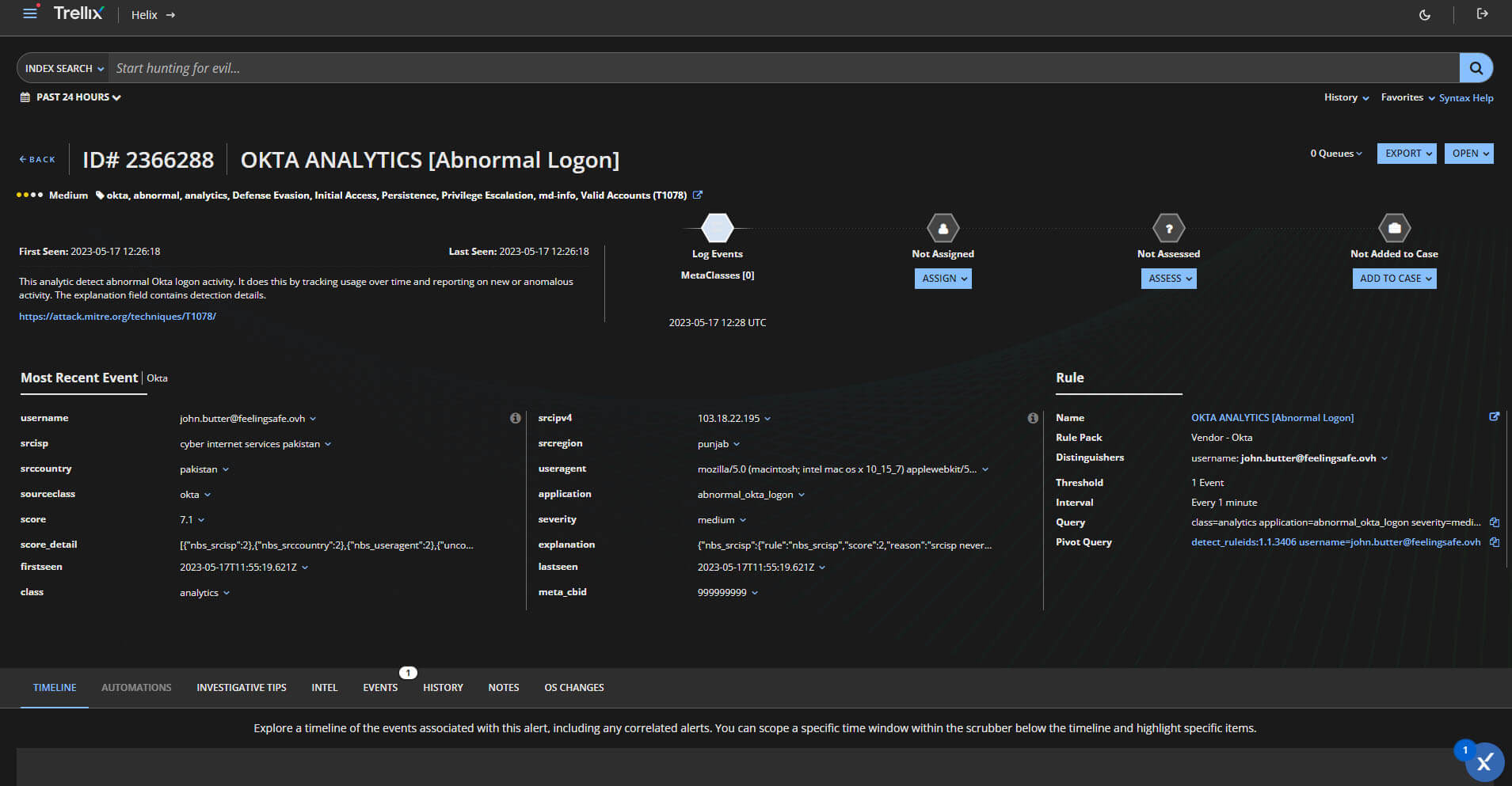
Identify what rule corresponds to an Adaptive Threat Protection and Threat Intelligence Exchange event





.png?revision=1)